Our comprehensive cyber security monitoring services extend far beyond compliance monitoring to deliver businesses with proactive detection of threats, reduced incident response time and an in-depth evaluation of existing security measures. Avoid the risk of unwanted downtime, security threats and network intrusion with our unique multi-layered approach to cyber monitoring. Our team will monitor your system using real-time threat intelligence to allow you more time to focus on core business functions.
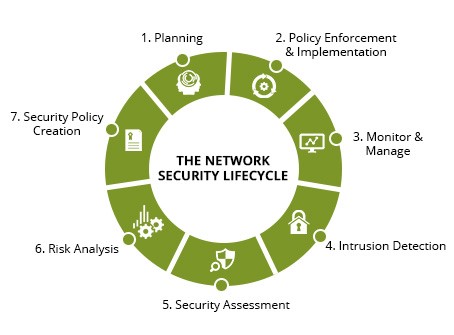
As these threats are not always avoidable and often unexpected, it is the responsibility of these businesses to take the necessary measures to protect their livelihood. Troy defends against modern cyber threats and effectively consults our clients through a proven methodology to ensure security compliance. Monitoring allows your business to remain in accordance with organizational policies, as well as comply with regulatory or legal requirements. We manage security risks in several ways, such as by:
-
Establishing a monitoring strategy based on assessment of risk and business needs.
-
Monitoring all systems, networks, and services to ensure full security coverage.
-
Monitoring both inbound and outbound network traffic to quickly identify unusual trends or activities.
-
Monitoring user activity to identify accidental or unauthorized misuse of data or systems.
-
Keeping a record of events and generating alerts to inform clients of possible security issues.